Critical Infrastructure Protection: Agencies Need to Enhance Oversight of Ransomware Practices and Assess Federal Support
Fast Facts
Ransomware—software that makes data and systems unusable unless ransom is paid—can severely impact government operations and critical infrastructure. Such attacks have led to significant financial losses, health care disruptions, and more.
Most federal agencies that lead and manage risk for 4 critical sectors—manufacturing, energy, healthcare and public health, and transportation systems—have assessed or plan to assess risks associated with ransomware. But agencies haven't fully gauged the use of leading cybersecurity practices or whether federal support has mitigated risks effectively in the sectors.
Our recommendations address these issues.

Highlights
What GAO Found
Ransomware—software that makes data and systems unusable unless ransom payments are made—is having increasingly devastating impacts. For example, the Department of the Treasury reported that the total value of U.S. ransomware-related incidents reached $886 million in 2021, a 68 percent increase compared to 2020 (see figure).
Treasury Reported Dollar Value of U.S. Ransomware-Related Incidents
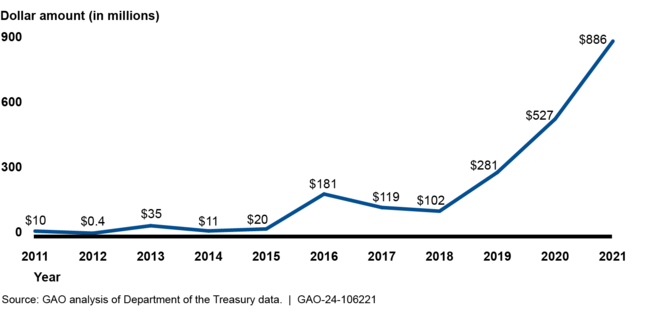
In addition to monetary losses, ransomware has led to other impacts, such as the inability to provide emergency care when hospital IT systems are unusable. The FBI reported that 870 critical infrastructure organizations were victims of ransomware in 2022, affecting 14 of the 16 critical infrastructure sectors. Among those incidents, almost half were from four sectors—critical manufacturing, energy, healthcare and public health, and transportation systems. The full impact of ransomware is likely not known because reporting is generally voluntary. The Department of Homeland Security is planning to issue new reporting rules by March 2024 that could provide a more complete picture of ransomware's impact.
The four selected sectors' adoption of leading practices to address ransomware is largely unknown. None of the federal agencies designated as the lead for risk management for selected sectors have determined the extent of adoption of the National Institute of Standards and Technology's recommended practices for addressing ransomware. Doing so would help the lead federal agencies be a more effective partner in national efforts to combat ransomware.
Most of the six selected lead federal agencies have assessed or plan to assess risks of cybersecurity threats including ransomware for their respective sectors, as required by law. Regarding lead agencies assessing their support of sector efforts to address ransomware, half of the agencies have evaluated aspects of their support. For example, agencies have received and assessed feedback on their ransomware guidance and briefings. However, none have fully assessed the effectiveness of their support to sectors, as recommended by the National Infrastructure Protection Plan. Fully assessing effectiveness could help address sector concerns about agency communication, coordination, and timely sharing of threat and incident information.
Why GAO Did This Study
The nation's 16 critical infrastructure sectors provide essential services such as electricity, healthcare, and gas and oil distribution. However, cyber threats to critical infrastructure, such as ransomware, represent a significant national security challenge.
This report (1) describes the reported impact of ransomware attacks on the nation's critical infrastructure, (2) assesses federal agency efforts to oversee sector adoption of leading federal practices, and (3) evaluates federal agency efforts to assess ransomware risks and the effectiveness of related support.
To do so, GAO selected four critical infrastructure sectors—critical manufacturing, energy, healthcare and public health, and transportation systems. For each sector, GAO analyzed documentation, such as incident reporting and risk analysis, and compared efforts to leading cybersecurity guidance. GAO also interviewed sector and federal agency officials to obtain information on ransomware-related impacts, practices, and support.
Recommendations
GAO is making 11 recommendations to four agencies to, among other things, determine selected sectors' adoption of cybersecurity practices. DHS and HHS agreed with their recommendations. DOE partially agreed with one recommendation and disagreed with another. DOT agreed with one recommendation, partially agreed with one, and disagreed with a third. GAO continues to believe that the recommendations are valid.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of Energy | The Secretary of Energy should, in coordination with CISA and sector entities, determine the extent to which the energy sector is adopting leading cybersecurity practices that help reduce the sector's risk of ransomware. (Recommendation 1) |
DOE partially agreed with our recommendation. As of August 2024, DOE has not identified actions taken or planned in response to this recommendation. We will continue to monitor the status of this recommendation.
|
| Department of Energy | The Secretary of Energy should, in coordination with CISA and sector entities, develop and implement routine evaluation procedures that measure the effectiveness of federal support in helping reduce the risk of ransomware to the energy sector. (Recommendation 2) |
DOE disagreed with our recommendation. As of August 2024, DOE has not identified actions taken or planned in response to this recommendation. We will continue to monitor the status of this recommendation.
|
| Department of Health and Human Services | The Secretary of Health and Human Services should, in coordination with CISA and sector entities, determine the extent to which the healthcare and public health sector is adopting leading cybersecurity practices that help reduce the sector's risk of ransomware. (Recommendation 3) |
HHS agreed with our recommendation. In July 2024, the department stated that it believes it has met the intent of our recommendation through prior efforts, including its April 2023 Hospital Cyber Resiliency Initiative Landscape Analysis and version 2.0 of its Risk Identification and Site Criticality its toolkit. However, our January 2024 report noted that while the landscape analysis identified categories of the NIST cybersecurity framework that the sector is adopting, HHS was not yet tracking the adoption of specific ransomware practices within those categories. According to HHS, its Risk Identification and Site Criticality toolkit allows the department to analyze aggregate data and assess implementation of key NIST cybersecurity framework concepts, including those that will reduce the risk of ransomware. As of July 2024, HHS has not provided supporting documentation of its analysis of data obtained through the toolkit.
|
| Department of Health and Human Services | The Secretary of Health and Human Services should, in coordination with CISA and sector entities, develop and implement routine evaluation procedures that measure the effectiveness of federal support in helping reduce the risk of ransomware to the healthcare and public health sector. (Recommendation 4) |
HHS agreed with our recommendation. In July 2024, HHS stated that the department continues to work with its components, CISA, and sector entities, as appropriate, to develop and implement procedures to routinely evaluate the effectiveness of federal support in reducing the risk or ransomware to the Healthcare and Public Health Sector. HHS intends to provide updates to GAO in its biannual updates on these efforts. We will continue to monitor the status of this recommendation.
|
| Department of Homeland Security | The Secretary of Homeland Security should, in coordination with CISA and sector entities, determine the extent to which the critical manufacturing sector is adopting leading cybersecurity practices that help reduce the sector's risk of ransomware. (Recommendation 5) |
DHS agreed with our recommendation. In July 2024, DHS stated that the agency released its cross-sector Cybersecurity Performance Goals (CPGs) in October 2022, which are voluntary practices that outline the highest-priority measures that critical infrastructure owners and operators can implement to protect themselves against cyber threats, including ransomware. DHS stated that it plans to measure each critical infrastructure sector's implementation of CPGs through data obtained from the entities' enrollment in its cybersecurity review and assessment services, and potentially commercially available risk management data in the future. Further, DHS stated that it is working to update its CPGs by March 31, 2025, to ensure clear alignment with the National Institute of Standards and Technology's latest version of its Cybersecurity Framework, which was released February 26, 2024. We will continue to monitor the status of this recommendation.
|
| Department of Homeland Security | The Secretary of Homeland Security should, in coordination with CISA and sector entities, develop and implement routine evaluation procedures that measure the effectiveness of federal support in helping reduce the risk of ransomware to the critical manufacturing sector. (Recommendation 6) |
DHS agreed with our recommendation. In July 2024, DHS stated that it has collected feedback through several mechanisms, including its stakeholder engagement survey, the Cybersecurity Performance Goals (CPG) webpage, and collaboration with government and industry stakeholders in drafting version 2.0 of the CPGs. While these are positive steps, DHS has not yet provided support of its that it developed and implemented routine evaluation procedures measuring the effectiveness of federal support in reducing the risk of ransomware for the critical manufacturing sector. We will continue to monitor the status of this recommendation.
|
| Department of Homeland Security | The Secretary of Homeland Security should, in coordination with CISA, co-SRMAs, and sector entities, determine the extent to which the transportation systems sector is adopting leading cybersecurity practices that help reduce the sector's risk of ransomware. (Recommendation 7) |
DHS agreed with our recommendation. In July 2024, DHS stated that the agency released its cross-sector Cybersecurity Performance Goals (CPGs) in October 2022, which are voluntary practices that outline the highest-priority measures that critical infrastructure owners and operators can implement to protect themselves against cyber threats, including ransomware. DHS stated that it plans to measure each critical infrastructure sector's implementation of CPGs through data obtained from the entities' enrollment in its cybersecurity review and assessment services, and potentially commercially available risk management data in the future. Further, DHS stated that it is working to update its CPGs by March 31, 2025, to ensure clear alignment with the National Institute of Standards and Technology's latest version of its Cybersecurity Framework, which was released February 26, 2024. We will continue to monitor the status of this recommendation.
|
| Department of Homeland Security | The Secretary of Homeland Security should, in coordination with CISA, co-SRMAs, and sector entities, develop and implement routine evaluation procedures that measure the effectiveness of federal support in helping reduce the risk of ransomware to the transportation systems sector. (Recommendation 8) |
DHS agreed with our recommendation . In July 2024, DHS stated that it has collected feedback through several mechanisms, including its stakeholder engagement survey, the Cybersecurity Performance Goals (CPG) webpage, and collaboration with government and industry stakeholders in drafting version 2.0 of the CPGs. While these are positive steps, DHS has not yet provided support that it developed and implemented routine evaluation procedures measuring the effectiveness of federal support in reducing the risk of ransomware for the transportation systems sector. We will continue to monitor the status of this recommendation.
|
| Department of Transportation | The Secretary of Transportation should, in coordination with CISA, co-SRMAs, and sector entities, assess ransomware risks to the transportation systems sector. (Recommendation 9) |
DOT agreed with our recommendation. In June 2024, DOT stated that the department is will leverage weekly meetings with its co-SRMA partners within the Department of Homeland Security to coordinate and identify opportunities to provide complementary perspective or actions related to the Department of Homeland Security's efforts to assess ransomware risks to the transportation systems sector. DOT stated that such efforts align with the National Security Memorandum on Critical Infrastructure Security and Resilience (NSM-22), released April 30, 2024, which called for various risk-focused actions across sectors, including the transportation systems sector. Further, DOT stated that the Department will work with its co-SRMA partners to develop sharable initial outcomes of ongoing actions by September 30, 2025. We will continue to monitor the status of this recommendation.
|
| Department of Transportation | The Secretary of Transportation should, in coordination with CISA, co-SRMAs, and sector entities, determine the extent to which the transportation systems sector is adopting leading cybersecurity practices that help reduce the sector's risk of ransomware. (Recommendation 10) |
DOT disagreed with our recommendation. In June 2024, DOT reiterated that it believes that determining measures of adoption would only provide a snapshot in time. DOT also reiterated its concerns that the department and co-sector risk management agencies (SRMA) can neither verify nor cite voluntary information as comprehensive. The department noted that it can highlight the existing best practices readily available to mitigate ransomware risks through its co-SRMA efforts to implement risk management activities as part the National Security Memorandum on Critical Infrastructure Security and Resilience (NSM-22). As we reported, DOT's plan to encourage leading cybersecurity practices may help spread awareness, this approach does not assess the sector's adoption of the practices. A snapshot evaluation would still have value because it can help determine the sector's initial level of adoption of the practices and establish a baseline for DOT's assessment of sector risks. Further, even collecting limited, voluntary information from the sector can help SRMAs to better identify gaps, assess risks, and prioritize cybersecurity-related support. Improving its understanding of the transportation systems sector's practices that address ransomware will make DOT a more effective partner in national efforts to combat ransomware. We continue to believe that our recommendation is warranted. We will continue to monitor the status of this recommendation.
|
| Department of Transportation | The Secretary of Transportation should, in coordination with CISA, co-SRMAs, and sector entities, develop and implement routine evaluation procedures that measure the effectiveness of federal support in helping reduce the risk of ransomware to the transportation systems sector. (Recommendation 11) |
DOT partially agreed with our recommendation. In June 2024, DOT reiterated that assessing federal support within the transportation systems sector would require a cross-sector lead such as DHS. According to DOT, it agreed to collaborate with DHS and sector entities to help address the recommendation. We will continue to monitor the status of this recommendation.
|
