Critical Infrastructure Protection: EPA Urgently Needs a Strategy to Address Cybersecurity Risks to Water and Wastewater Systems
Fast Facts
A cyberattack on U.S. drinking and wastewater systems could, for example, produce drinking water with unsafe levels of bacteria or chemicals. Nations, cybercriminals, and others have targeted some of the nearly 170,000 U.S. water systems, which are increasingly automated.
EPA leads water cybersecurity efforts. It has worked with the water sector to improve cybersecurity. However, EPA hasn't identified and prioritized the greatest risks sector-wide. It also relies on water systems to voluntarily agree to improve cybersecurity.
We recommended that EPA develop a national cybersecurity strategy, assess whether it needs more authority, and more.
Cyberattacks on Water and Wastewater Systems Can Have Consequences for Public Health and the Environment

Highlights
What GAO Found
The water sector faces increasing cybersecurity-related risk. While national reporting requirements for cyber incidents are being developed, known incidents have disrupted water sector operations. Nations (including Iran and China), cybercriminals, and others have targeted water systems. For example, foreign hackers targeted multiple water systems in late 2023. Cyberattacks threaten public health, the environment, and other critical infrastructure sectors.
Water and Wastewater Systems' Vulnerability to Cyberattacks
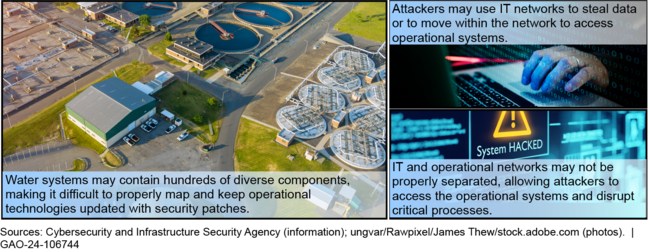
Federal agencies and other entities have acted to improve water sector cybersecurity, but reported challenges such as workforce skills gaps and older technologies that are difficult to update with cybersecurity protections. Further, the sector has made limited investments in cybersecurity protections because water systems prioritize funding to meet regulatory requirements for clean and safe water, while improving cybersecurity is voluntary. In a May 2024 alert, the Environmental Protection Agency (EPA) said it planned to increase enforcement activities to ensure drinking water systems address cybersecurity threats.
EPA has assessed aspects of cybersecurity risk but has not conducted a comprehensive sector-wide risk assessment or developed and used a risk-informed strategy to guide its actions. EPA is required by law, as well as National Security Memorandum 22 (NSM-22), to identify, assess, and prioritize water sector risk. EPA official said they have assessed threats, vulnerabilities, and consequences, but have not integrated this work in a comprehensive assessment. Without a risk assessment and strategy to guide its efforts, EPA has limited assurance its efforts address the highest risks.
EPA has faced challenges using its existing legal authority and voluntary approaches to manage cybersecurity risks but has not fully evaluated either approach. In March 2023, EPA interpreted existing legal requirements to include cybersecurity assessments at drinking water systems but withdrew the requirement 7 months later after facing legal challenges. Previous requirements and NSM-22 direct EPA to identify the authorities it needs to compel the sector to address risks. In July 2024, EPA officials said they had evaluated their authorities and would release the evaluation in 2025 with their risk assessment and strategy. Doing so and seeking additional authority as necessary can help EPA ensure the water sector is better prepared for any future cyberattacks.
Why GAO Did This Study
Recent cyber incidents highlight the vulnerability of the 170,000 water and wastewater systems in the U.S. water sector. EPA is responsible for leading, coordinating, and supporting activities to reduce cybersecurity risk to the water sector. The agency works in partnership with the Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) and other federal, state, and local entities.
GAO was asked to review cybersecurity threats facing the water sector and the federal government's efforts to address these threats. This report (1) describes cybersecurity risks and incidents; (2) examines actions by selected federal and nonfederal entities to improve cybersecurity; and (3) evaluates EPA's actions to address known risks.
GAO analyzed documents from EPA, CISA, and other entities on cyber threats, threat actors, and sector efforts to reduce risk. GAO interviewed federal and nonfederal officials with relevant cybersecurity responsibilities. GAO also visited and interviewed officials from large and small systems selected to provide varying perspectives.
Recommendations
GAO is making four recommendations, including that EPA assess sector risk; develop and implement a national cybersecurity strategy; and evaluate the sufficiency of its legal authorities to carry out its cybersecurity responsibilities and seek additional authority as necessary. EPA concurred with the recommendations and said it is taking action to complete them.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Environmental Protection Agency | The Administrator of EPA should, as required by law, conduct a water sector risk assessment, considering physical security and cybersecurity threats, vulnerabilities, and consequences. (Recommendation 1) |
In its comments on the report, EPA stated that it concurs with this recommendation. It will develop a risk assessment and risk management plan that address cybersecurity in accordance with the National Security Memorandum on Critical Infrastructure Security and Resilience published in April 2024.
|
| Environmental Protection Agency | The Administrator of EPA should develop and implement a risk-informed cybersecurity strategy, in coordination with other federal and sector stakeholders, to guide its water sector cybersecurity programs. Such a strategy should include information from a risk assessment and should identify objectives, activities, and performance measures; roles, responsibilities, and coordination; and needed resources and investments. (Recommendation 2) |
In its comments on the report, EPA said it concurs with the recommendation and will develop a water sector risk assessment and risk management plan that address cybersecurity in accordance with the National Security Memorandum on Critical Infrastructure Security and Resilience, published April 2024.
|
| Environmental Protection Agency | The Administrator of EPA should evaluate its existing legal authorities for carrying out EPA's cybersecurity responsibilities and seek any needed enhancements to such authorities from the administration and Congress. (Recommendation 3) |
In its comments on the report, EPA stated that it concurs with this recommendation. It also said that it had already conducted a thorough examination of and provided technical assistance to Congress on existing legal authorities with respect to EPA cybersecurity responsibility. Further, the agency committed to providing a detailed explanation of its examination of legal authorities as part of the risk management plan, to be completed in 2025. Until this explanation is completed and available, however, GAO cannot assess the degree to which EPA has examined its legal authorities. GAO will continue to follow up on this recommendation.
|
| Environmental Protection Agency | The Administrator of EPA should submit the Vulnerability Self-Assessment Tool (VSAT) for independent peer review and revise the tool as appropriate. (Recommendation 4) |
In its comments on the report, EPA stated that it concurs with this recommendation. It said it will submit the VSAT tool for independent peer review and revise the tool as appropriate. EPA estimated the review will begin in November 2024. GAO will follow up on the status of this recommendation.
|
