Cybersecurity: State Needs to Expeditiously Implement Risk Management and Other Key Practices
Fast Facts
The State Department carries out American diplomacy and helps shape U.S. foreign policy. Securing the IT systems that support State's mission is crucial to its ability to manage its cybersecurity risks.
But State hasn't fully implemented its cybersecurity risk program. We found that it needs to:
- Implement processes to detect and respond to cybersecurity incidents
- Update hardware and software that aren't supported by vendors
- Strengthen the Chief Information Officer's ability to manage and oversee all IT infrastructure
- Better communicate IT-related requirements to its overseas posts
Our 15 recommendations address these and other issues.

Highlights
What GAO Found
The Department of State has documented a cybersecurity risk management program that meets federal requirements. Specifically, the department has identified risk management roles and responsibilities and developed a risk management strategy. However, State has not fully implemented its program to identify and monitor risk to assets and the information maintained on its systems, as shown in the figure below.
Examples of State's Progress in Implementing Its Cybersecurity Risk Management Program

Until the department implements required risk management activities, it lacks assurance that its security controls are operating as intended. Moreover, State is likely not fully aware of information security vulnerabilities and threats affecting mission operations.
State's incident response processes for detecting, responding to, and recovering from cybersecurity incidents generally align with federal guidance by requiring the department to establish an incident handling capability for its information systems. For example, State's Cyber Incident Response Team and other units within its Monitoring and Incident Response Division provide the capability to identify active and potential threats to the department's network security 24 hours a day, 7 days a week.
However, the department has not fully implemented processes that support its incident response program. For example, State has not fully updated and tested information system contingency plans to ensure continuity of operations nor configured its centralized inventory management database to identify asset inventory information from all available data sources.
Further, State has not adequately secured its IT infrastructure to support its incident response program. This includes replacing the 23,689 hardware systems and 3,102 occurrences of network and server operating system software installations that have reached end-of-life. Certain installations of operating system software had reached end-of-life over 13 years ago.
Without fully implemented incident response processes and an adequately secured IT infrastructure to support State's incident response program by, among other things, updating outdated or unsupported products, State's IT infrastructure is vulnerable to exploits. Furthermore, the department risks being unable to fully detect, investigate, and mitigate cybersecurity-related incidents.
In the last several years, State has taken a number of steps to clarify and strengthen the role of the Chief Information Officer (CIO). For example, in October 2020, State issued a memo and matrix outlining the roles and responsibilities for cybersecurity of State's CIO and others.
Nevertheless, the ability of State's CIO to secure the department's IT systems is limited due to shared management responsibilities and a lack of communication. In State's IT structure, the CIO manages State's main network and sets department-wide standards, but bureaus perform many activities independently, purchasing much of their own equipment, managing many of their own IT systems, and obtaining their own funding. In addition, a lack of communication among the CIO, Information Resource Management, and the bureaus also hampers the CIO's ability to secure the department's IT systems. For example, this created confusion among information system security officers about the applicability of IT-related requirements. State's IT structure, insulated culture (i.e., bureaus operating independently), and the lack of communication between the CIO and the bureaus is responsible for many of the deficiencies identified in this report, as shown in the figure below.
Examples of Deficiencies at State Due to Its IT Structure and Insulated Culture
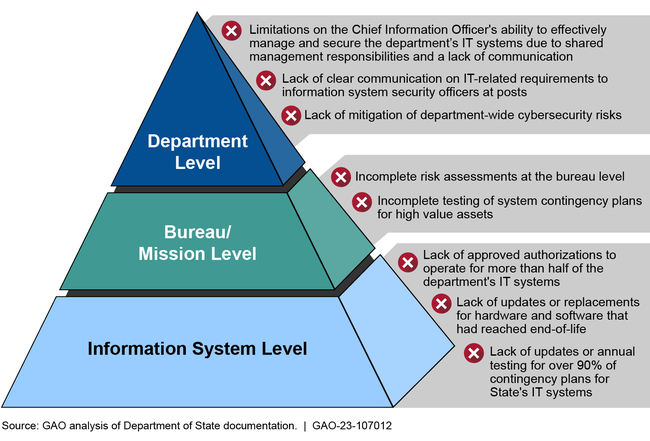
In October 2021, the CIO noted that the roles and responsibilities matrix needed to be updated to better reflect the specific cyber functions and activities that department leadership and bureaus engage in throughout State. Until State addresses these and other deficiencies, the CIO faces challenges managing and overseeing the department's cybersecurity program, including risk management and incident response, and the department's systems remain vulnerable.
Why GAO Did This Study
The security of State's IT systems is vital to promoting an open, interoperable, and reliable information and communications infrastructure in the department.
GAO was asked to review State's cybersecurity practices. This report assesses the extent to which (1) State has implemented a cybersecurity risk management program; (2) State has a process and supporting infrastructure to detect, respond to, and recover from cybersecurity incidents; and (3) State's Chief Information Officer (CIO) is able to secure its IT systems department-wide.
To conduct this work, GAO reviewed federal laws and guidance and compared them to department policies. GAO also analyzed samples of IT risk, incident response, and configuration data for selected enterprise-wide systems and 16 embassies and consular locations. Additionally, GAO interviewed State officials from the Bureau of Information Resource Management and the Bureau of Diplomatic Security with primary responsibility for managing and securing State's IT systems and networks. GAO also met with high-level officials at the Bureau of Consular Affairs, given that it operates more IT systems than any other bureau.
This is a public version of a sensitive report with limited distribution. In response to a request from State officials, GAO excluded from this public report information deemed sensitive, such as specific post locations, system names, and technologies as well as a specific weakness.
Recommendations
GAO is making 15 recommendations to State, including that the Secretary of State
- develop plans to mitigate vulnerabilities that State previously identified,
- conduct bureau-level risk assessments for the 28 bureaus that owned information systems that GAO reviewed,
- ensure that its information systems have valid authorizations to operate in accordance with department policies and federal guidance,
- ensure that the CIO has access to assets at bureaus and posts to continuously monitor for threats and vulnerabilities that may affect mission operations,
- ensure that all system contingency plans for high value assets are tested annually as required by department policies, and
- direct the CIO to update an October 2020 matrix to better ensure compliance with applicable department policies and federal guidance.
State concurred with all 15 recommendations to address cybersecurity weaknesses and provided technical comments, which were incorporated as appropriate.
In addition, GAO will issue a subsequent limited distribution report discussing technical security control deficiencies in State's IT infrastructure. The report will identify approximately 40 unique deficiencies across three bureaus and 16 posts and will address about 500 recommendations to State for remediating those deficiencies. These recommendations will include replacing hardware and software installations that have reached end-of-life.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of State |
Priority Rec.
The Secretary of State should direct the CIO to develop and maintain a department-wide risk profile that prioritizes the department's most significant risks, including the areas of exposure and threats that State identified, consistent with federal requirements. (Recommendation 1) |
The State Department concurred with this recommendation. In February 2024, the department stated that it has planned for and is working towards the completion of six additional risk profiles and the integration of all areas of exposure and threats with its Enterprise Risk Profile by December 2024. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State | The Secretary of State should direct the CIO to develop plans to mitigate vulnerabilities in the areas of exposure and threats that State previously identified. (Recommendation 2) |
The State Department concurred with this recommendation. In February 2024, the department stated that it has taken steps to address each area of exposure that include defining cybersecurity roles and responsibilities and implementing processes and tools to better manage cybersecurity risks across the enterprise. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State | The Secretary of State should direct the CIO to conduct bureau-level risk assessments for the 28 bureaus that owned information systems that we reviewed. (Recommendation 3) |
The State Department concurred with this recommendation. In February 2024, the department stated that four bureau-level cyber risk assessments had been completed in August 2023 and that they anticipate assessing all bureaus by the end of FY 2025. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State | The Secretary of State should direct the CIO to ensure that system security plans for the two systems we identified are updated at least annually as required by department policies. (Recommendation 4) |
The State Department concurred with this recommendation. In February 2024, the department stated that its Governance, Risk Management, and Compliance (GRC) platform automatically updates system security plans (SSP) whenever an approved change is made. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State |
Priority Rec.
The Secretary of State should direct the CIO to ensure that State's information systems have valid authorizations to operate in accordance with department policies and federal guidance. (Recommendation 5) |
The State Department concurred with this recommendation. In February 2024, the department stated that it had made significant progress on increasing the percentage of systems with valid authorizations. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State | The Secretary of State should direct the CIO to assess, prioritize, and allocate available department-wide resources to address the constraints that contribute to the backlog of its assessment and authorization process and coordinate these activities with the Bureau of Budget and Planning. (Recommendation 6) |
The State Department concurred with this recommendation. In February 2024, the department stated that it had significantly reduced the backlog of authorizations through the allocation and prioritization of resources. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State | The Secretary of State should direct the CIO to update the department's continuous monitoring strategy to define and document minimum frequency requirements for continuous monitoring of security controls and ensure the implementation of these requirements across department systems. (Recommendation 7) |
The State Department concurred with this recommendation. In February 2024, the department stated that its Continuous Monitoring Strategy of Assessment and Authorization defines security monitoring frequencies for metrics and risk management. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State |
Priority Rec.
The Secretary of State should direct the CIO to implement all components of State's Information Security Continuous Monitoring program across the department, including the continuous diagnostic and mitigation capabilities, in accordance with department policies and federal guidance. (Recommendation 8) |
The State Department concurred with this recommendation. In February 2024, the department stated that it maintains a documented Information Security Continuous Monitoring (ISCM) strategy and has implemented a Continuous Diagnostic and Mitigation (CDM) dashboard that provides updated threat and vulnerability information across the enterprise. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State | The Secretary of State should ensure that the CIO has access to assets at bureaus and posts to continuously monitor for threats and vulnerabilities that may affect mission operations. (Recommendation 9) |
The State Department concurred with this recommendation. In February 2024, the department stated it has implemented and currently operates a Continuous Diagnostic and Mitigation (CDM) Dashboard, which displays all bureau and post assets. According to the department, the dashboard is available to the CIO and other authorized personnel as appropriate. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State | The Secretary of State should direct the Assistant Secretary of State for Diplomatic Security to ensure that State's incident response procedures are tested annually in accordance with department policies. (Recommendation 10) |
The State Department concurred with this recommendation. In February 2024, the department stated that its incident response procedures are tested annually with identified improvements added through version updates to its cyber incident response plan. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State | The Secretary of State should direct the CIO to annually update the information system contingency plan for the one system we identified in accordance with department policies and federal guidance. (Recommendation 11) |
The State Department concurred with this recommendation. In February 2024, the department stated that the contingency plan for the identified information system was updated and tested in February 2023. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State | The Secretary of State should direct the CIO to annually test the contingency plan for the one system we identified in accordance with department policies. (Recommendation 12) |
The State Department concurred with this recommendation. In February 2024, the department stated that the contingency plan test for the system identified was completed in September 2023 and that they have recently provided documentation to GAO. Once we have reviewed the documentation for completeness and verify State's corrective actions, we will update the recommendation's status.
|
| Department of State | The Secretary of State should direct the Assistant Secretary of State for Diplomatic Security to ensure that contingency plans for all HVA systems are tested annually as required by department policies. (Recommendation 13) |
The State Department concurred with this recommendation. In February 2024, the department stated that it had retired several HVAs and that all but five are current in their annual contingency plan testing assessments. The department also mentioned that it planned to further emphasize compliance by adding annual contingency plan testing as a grading metric to its bureau scorecards. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State | The Secretary of State should direct the CIO to update the October 2020 matrix to better ensure compliance with applicable department policies and federal guidance. The update could involve operationalizing the matrix describing the roles and responsibilities of the various bureaus so that the department as a whole can better address cybersecurity requirements. (Recommendation 14) |
The State Department concurred with this recommendation. In February 2024, the department stated that its offices responsible for information technology and cybersecurity would collaborate to make any additions or revisions to accurately depict the specific duties outlined in its cybersecurity roles and responsibilities matrix. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
| Department of State | The Secretary of State should direct the CIO and the Assistant Secretary for DS to ensure that IRM and DS provide more effective communication about the operation of IT systems to information system security officers at overseas posts regarding department policies and guidance. (Recommendation 15) |
The State Department concurred with this recommendation. In February 2024, the department stated that it has developed several communication channels to assist overseas information systems security officers (ISSOs) with awareness regarding policies and guidance related to IT systems. The department also mentioned other actions to increase communication such as implementing a SharePoint site dedicated to domestic and overseas ISSO personnel. State has not yet provided evidence of its corrective actions. We will continue to monitor the department's progress and update the recommendation's status when we receive evidence of State's corrective actions.
|
