Science & Tech Spotlight: Zero Trust Architecture
Fast Facts
Zero trust architecture (ZTA) is a cybersecurity approach that authenticates and authorizes every interaction between a network and a user or device—in contrast to traditional cybersecurity models that allow users or devices to move freely within the network once they are granted access. ZTA works on the "never trust, always verify" principle and assumes that attacks will come from within and outside of the network.
ZTA could provide better protection of an organization's data and systems, but it may be difficult to implement because there is no widely accepted definition of what a fully functional ZTA looks like in practice.

Highlights
Why This Matters
IT systems are vital to the functioning of the federal government, critical infrastructure, and the economy. As IT systems become larger and more complex, they have become more susceptible to cyberattacks. Zero trust architecture is a cybersecurity approach that assumes breaches will occur and uses risk-based access controls to limit the damage from an attack.
The Technology
What is it? Zero trust architecture (ZTA) is a cybersecurity approach intended to address the rapidly evolving security risks faced by IT systems worldwide. These risks include insider threats from employees who either deliberately or unintentionally create a security breach and new, more sophisticated and persistent threats from around the globe. Further, the need to access resources from anywhere, at any time, and with any device has led to increasingly complex IT systems. Because of these and other risks, GAO continues to designate information security as a government-wide high-risk area, including the protection of critical infrastructure from cyber threats and the privacy of personally identifiable information.
The ZTA approach focuses on authenticating and authorizing every interaction between network resources and a user or device. Traditional, perimeter-based cybersecurity models can allow users or devices to move freely within the network once they are granted access. However, building stronger perimeters is no longer sufficient to protect networks, users, applications, and data. In contrast to traditional models, ZTA functions on the principle "never trust, always verify" and assumes that attacks will come from within and outside the network (see fig. 1).
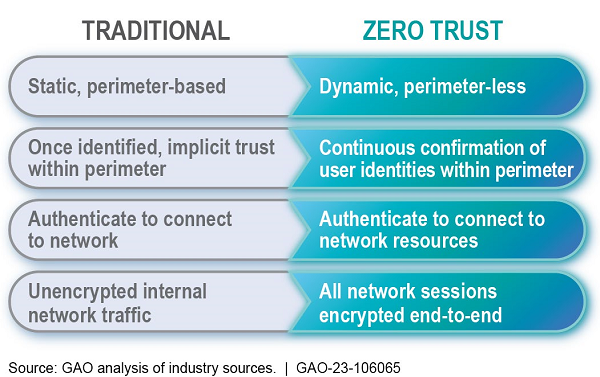
Figure 1. Comparison of traditional and zero trust cybersecurity architectures.
How does it work? ZTA aims to continuously monitor and protect all activity and resources on an IT network. Given the increasingly complex nature of IT networks, including cloud and hybrid environments, ZTA's goals are to reduce opportunities for attackers by restricting access and to detect attacks by monitoring user behavior and other network activity.
Organizations that use ZTA establish security policies that are applied by a trust algorithm, which ultimately grants or denies access to a resource. The algorithm uses several supporting technologies (see fig. 2), including the following:
- An identity, credential, and access management (ICAM) system grants access to certain network resources at certain times based on user information. For example, it may use multi-factor authentication or facial recognition to determine that a specific user is entitled to access.
- Security analytics uses threat intelligence, activity logs, traffic inspection, and other information about the network and its resources to detect unusual patterns. For example, data analytics and artificial intelligence techniques identify anomalies that could warrant further investigation.
- Endpoint protection ensures that the devices (the endpoints) and their data are protected from threats and attacks. Endpoint protection may include monitoring for intrusions, known vulnerabilities, and malware.
- Encryption prevents unauthorized data disclosure, modification, and access.
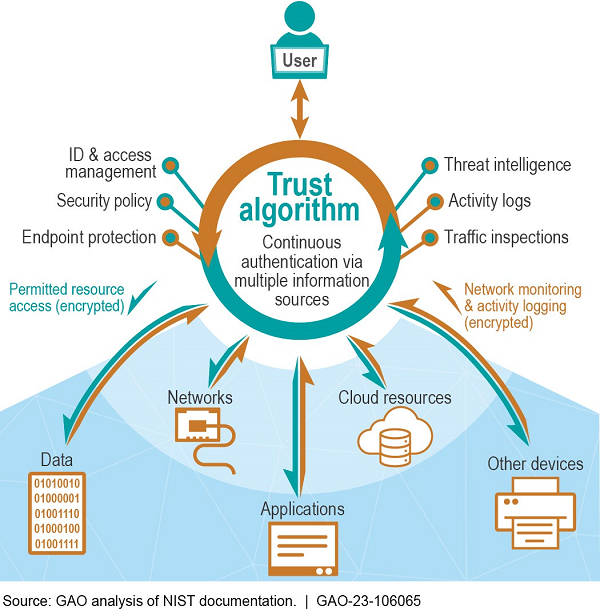
Figure 2. A schematic of how zero trust architecture could control access to network resources.
How mature is it? Commercial products needed for ZTA implementation are largely mature and available. However, ZTA is a systems approach to cybersecurity rather than a technology, and there is no single solution for a mature ZTA. Organizations attempting to implement ZTA have faced difficulties. For example, a National Institute of Standards and Technology (NIST) project to build and demonstrate examples of ZTA using products and technologies from different vendors found that many ICAM and endpoint protection technologies could not be integrated into a functional ZTA.
In addition, some technologies would need to be adapted to implement ZTA. For example, the National Cybersecurity Protection System, which defends the federal government from cyber threats, has intrusion prevention functions that are not compatible with ZTA. According to a NIST publication, the system was originally designed to work on the perimeters of government networks. To be compatible with ZTA, the system would need to be adapted to continuously monitor resources within the network. Further, machine-learning models—which are recommended for automated threat detection—would need to be tailored to each organization’s ZTA, a potentially time-consuming process.
The federal government has begun efforts to use ZTA. Since 2020, NIST and the Office of Management and Budget have issued direction and guidance to federal agencies on the use of ZTA. In addition, the Cybersecurity and Infrastructure Security Agency in 2021 issued a draft roadmap on transition to ZTA, and the 2022 National Defense Authorization Act directed the Department of Defense to develop a zero trust strategy and a model architecture.
Opportunities
- Confine possible security incidents. ZTA prevents users, processes, and devices from moving freely throughout a network after gaining access. Damage from any network intrusion will therefore be better contained.
- Improve situational awareness. ZTA can provide more visibility into resource usage, which can improve the detection of attacks and lead to more timely responses.
- Improve data confidentiality. With improved access controls and encryption, data will be more secure from both internal and external intrusion.
Challenges
- Resources needed to transition to ZTA. An organization implementing ZTA would need additional resources for computing as well as new tools, practices, and training, which can be expensive and time-consuming. For instance, to establish appropriate access policies, an organization would need to develop and maintain complete information about systems, networks, and data.
- Interoperability. Because there is no single ZTA solution, ZTA implementation requires integrating existing technologies with each other and with newer technologies. These technologies may not be designed to work together, particularly in organizations with large investments in traditional technologies.
- Standards. Governance frameworks and technical standards for ZTA are still emerging, and there is no consensus on how existing industry standards should be applied to a ZTA implementation.
Policy Context and Questions
- What is an appropriate level of oversight to ensure the proper implementation of ZTA?
- What are appropriate performance goals and measures to help justify investments in ZTA?
- What additional standards and frameworks are needed to facilitate ZTA design and implementation?
For more information, contact Brian Bothwell at (202) 512-6888 or BothwellB@gao.gov and Jennifer R. Franks at (404) 679-1831 or FranksJ@gao.gov.
