Critical Infrastructure: Actions Needed to Better Secure Internet-Connected Devices
Fast Facts
The nation's 16 critical infrastructure sectors rely on internet-connected devices and systems to deliver essential services, such as electricity and health care. These sectors face increasing cybersecurity threats—an issue on our High Risk list.
Federal agencies that have leadership roles in 3 sectors we reviewed have taken some steps to manage the cybersecurity risks posed by internet-connected devices and systems. But they've not assessed risks to the sectors as a whole. Without a holistic assessment, the agencies can't know what additional cybersecurity protections might be needed.
Our recommendations address this and more.

Highlights
What GAO Found
The nation's critical infrastructure sectors rely on electronic systems, including Internet of Things (IoT) and operational technology (OT) devices and systems. IoT generally refers to the technologies and devices that allow for the network connection and interaction of a wide array of “things,” throughout such places as buildings, transportation infrastructure, or homes. OT are programmable systems or devices that interact with the physical environment, such as building automation systems that control machines to regulate and monitor temperature.
Figure: Overview of Connected IT, Internet of Things (IoT), and Operational Technology
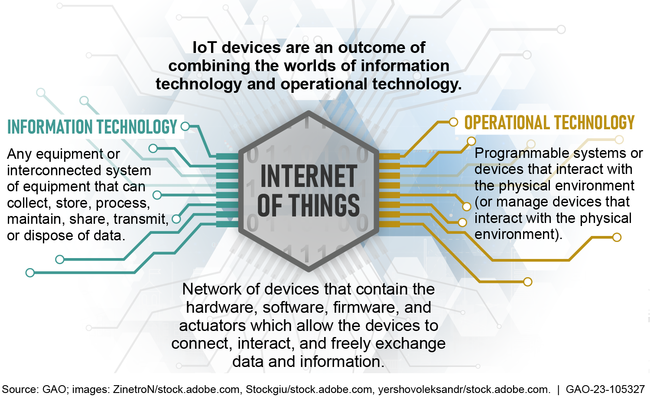
To help federal agencies and private entities manage the cybersecurity risks associated with IoT and OT, the Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) and the National Institute of Standards and Technology (NIST) have issued guidance and provided resources. Specifically, CISA has published guidance, initiated programs, issued alerts and advisories on vulnerabilities affecting IoT and OT devices, and established working groups on OT. NIST has published several guidance documents on IoT and OT, maintained a center of cybersecurity excellence, and established numerous working groups. In addition, the Federal Acquisition Regulatory Council is considering updates to the Federal Acquisition Regulation to better manage IoT and OT cybersecurity risks.
Selected federal agencies with a lead role have reported various cybersecurity initiatives to help protect three critical infrastructure sectors with extensive use of IoT or OT devices and systems.
Title: Sector Lead Agencies' Internet of Things (IoT) or Operational Technology (OT) Cybersecurity Initiatives
|
Sector (Lead Federal Agency) |
Examples of IoT or OT Initiatives |
|---|---|
|
Energy (Department of Energy) |
Considerations for OT Cybersecurity Monitoring Technologies guidance provides suggested evaluation considerations for technologies to monitor OT cybersecurity of systems that, for example, distribute electricity through the grid.
Cybersecurity for the Operational Technology Environment methodology aims to enhance energy sector threat detection of anomalous behavior in OT networks, such as electricity distribution networks. |
|
Healthcare and public health (Department of Health and Human Services) |
Pre-market Guidance for Management of Cybersecurity identifies issues related to cybersecurity for manufacturers to consider in the design and development of their medical devices, such as diagnostic equipment.
Post-market Management of Cybersecurity in Medical Devices provides recommendations for managing cybersecurity vulnerabilities for marketed and distributed medical devices, such as infusion pumps. |
|
Transportation systems (Departments of Homeland Security and Transportation) |
Surface Transportation Cybersecurity Toolkit is designed to provide informative cyber risk management tools and resources for control systems that, for example, function on the mechanics of the vessel.
Department of Homeland Security's Transportation Security Administration's Enhancing Rail Cybersecurity Directive requires actions, such as conducting a cybersecurity vulnerability assessment and developing of cybersecurity incident response plans for higher risk railroads. |
Source: GAO analysis of agency documentation │ GAO-23-105327
However, none of the selected lead agencies had developed metrics to assess the effectiveness of their efforts. Further, the agencies had not conducted IoT and OT cybersecurity risk assessments. Both of these activities are best practices. Lead agency officials noted difficulty assessing program effectiveness when relying on voluntary information from sector entities. Nevertheless, without attempts to measure effectiveness and assess risks of IoT and OT, the success of initiatives intended to mitigate risks is unknown.
The Internet of Things Cybersecurity Improvement Act of 2020 generally prohibits agencies from procuring or using an IoT device after December 4, 2022, if that device is considered non-compliant with NIST-developed standards. Pursuant to the act, in June 2021 NIST issued a draft guidance document that, among other things, provides information for agencies, companies and industry to receive reported vulnerabilities and for organizations to report found vulnerabilities. The act also requires the Office of Management and Budget (OMB) to establish a standardized process for federal agencies to waive the prohibition on procuring or using non-compliant IoT devices if waiver criteria detailed in the act are met.
As of November 22, 2022, OMB had not yet developed the mandated process for waiving the prohibition on procuring or using non-compliant IoT devices. OMB officials noted that the waiver process requires coordination and data gathering with other entities. According to OMB, it is targeting November 2022 for the release of guidance on the waiver process. Given the act's restrictions on agency use of non-compliant IoT devices beginning in December 2022, the lack of a uniform waiver process could result in a range of inconsistent actions across agencies.
Why GAO Did This Study
Cyber threats to critical infrastructure IoT and OT represent a significant national security challenge. Recent incidents—such as the ransomware attacks targeting health care and essential services during the COVID-19 pandemic—illustrate the cyber threats facing the nation's critical infrastructure. Congress included provisions in the IoT Cybersecurity Improvement Act of 2020 for GAO to report on IoT and OT cybersecurity efforts.
This report (1) describes overall federal IoT and OT cybersecurity initiatives; (2) assesses actions of selected federal agencies with a lead sector responsibility for enhancing IoT and OT cybersecurity; and (3) identifies leading guidance for addressing IoT cybersecurity and determines the status of OMB's process for waiving cybersecurity requirements for IoT devices. To describe overall initiatives, GAO analyzed pertinent guidance and related documentation from several federal agencies.
To assess lead agency actions, GAO first identified the six critical infrastructure sectors considered to have the greatest risk of cyber compromise. From these six, GAO then selected for review three sectors that had extensive use of IoT and OT devices and systems. The three sectors were energy, healthcare and public health, and transportation systems. For each of these, GAO analyzed documentation, interviewed sector officials, and compared lead agency actions to federal requirements.
GAO also analyzed documentation, interviewed officials from the selected sectors, and compared those sector's cybersecurity efforts to federal requirements. GAO also interviewed OMB officials on the status of the mandated waiver process.
Recommendations
GAO is making eight recommendations to the lead agencies of the reviewed sectors—the Departments of Energy, Health and Human Services, Homeland Security, and Transportation. GAO is recommending that each department (1) establish and use metrics to assess the effectiveness of sector IoT and OT cybersecurity efforts and (2) evaluate sector IoT and OT cybersecurity risks. GAO is also making one recommendation to OMB to expeditiously establish the required IoT cybersecurity waiver process.
The Departments of Homeland Security and Transportation concurred with the recommendations while Energy said it would not respond to the recommendations until after further coordination with other agencies. Health and Human Services neither agreed nor disagreed with the recommendations but noted planned actions. Specifically, the department said it planned to update its sector-specific plan but asserted that it cannot compel adoption of the plan in the private sector. GAO recognizes the voluntary character of the relationship between the department and the critical infrastructure sector. However, establishing IoT and OT specific metrics will provide a basis for the department to establish accountability, document actual performance, promote effective management, and provide a feedback mechanism to inform decision-making.
OMB stated that the agency is targeting November 2022 for release of guidance on the waiver process. As of November 22, 2022, OMB had not yet issued this guidance.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of Energy | The Secretary of Energy, as SRMA for the energy sector, should direct the Director of the Office of Cybersecurity, Energy Security, and Emergency Response to use the National Plan to develop a sector-specific plan that includes metrics for measuring the effectiveness of their efforts to enhance the cybersecurity of their sector's IoT and OT environments. (Recommendation 1) |
In April 2023, Energy noted that it was working with the U.S. Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) on updating the National Infrastructure Plan. It added that once the National Plan was updated, the agency would work toward updating its sector-specific plan. The agency stated that the sector-specific plan is estimated to be completed one year after the updated National Plan is published. According to the President's National Security Memorandum on Critical Infrastructure Security and Resilience in April 2024, the updated National Plan is due by April 2025.
|
| Department of Energy | The Secretary of Energy, as SRMA for the energy sector, should direct the Director of the Office of Cybersecurity, Energy Security, and Emergency Response to include IoT and OT devices as part of the risk assessments of their sector's cyber environment. (Recommendation 2) |
In July 2024, Energy stated that it considered IoT and OT devices as part of a sector risk analysis work completed in collaboration with industry through the utilization of Lawrence Livermore National Laboratory. Officials noted that the work is to be incorporated into a sector risk assessment that has been delayed due to delays with the Department of Homeland Security's Cybersecurity and Infrastructure Security Agency's update to the national critical infrastructure plan.
|
| Department of Health and Human Services | The Secretary of Health and Human Services, as SRMA for the healthcare and public health sector, should direct the Assistant Secretary for Preparedness and Response to use the National Plan to develop a sector-specific plan that includes metrics for measuring the effectiveness of their efforts to enhance the cybersecurity of their sector's IoT and OT environments. (Recommendation 3) |
In May 2023, HHS stated that the Assistant Secretary for Preparedness and Response (ASPR) was awaiting the release of the National Infrastructure Protection Plan to update the Sector Specific Plan for the Healthcare and Public Health Sector. HHS also stated that while ASPR does not have the authorities to mandate reporting or the resources to support a comprehensive effort to track the implementation or success of any activities related to IoT and OT, it will include considerations about IoT and OT as part of its all-hazards approach when it updates the Sector Specific Plan. In addition, the agency stated that it will continue to consult and coordinate with ASPR, other relevant HHS offices, and other federal agencies such as DHS/CISA and DOC/NIST to promote a collaborative approach to the larger cross-sector landscape. According to the President's National Security Memorandum on Critical Infrastructure Security and Resilience in April 2024, the updated National Plan is due by April 2025.
|
| Department of Health and Human Services | The Secretary of Health and Human Services, as SRMA for the healthcare and public health sector, should direct the Assistant Secretary for Preparedness and Response to include IoT and OT devices as part of the risk assessments of their sector's cyber environment. (Recommendation 4) |
In May 2023, HHS stated that the Assistant Secretary for Preparedness and Response (ASPR) will continue to rely heavily on partners within the agency, such as the HHS 405d program and the Healthcare Cyber Coordination Center (HC3), as well as external partners such as CISA and SCC members for risk assessment of environments which include IoT and OTs. In addition, the agency stated that ASPR is launching version 2.0 of the Risk Identification and Site Criticality (RISC) Tool, which includes a set of questions specific to cybersecurity that are aligned with the NIST Cybersecurity Framework. HHS stated that this all-hazards risk assessment tool can be enhanced with new content and functionality in response to recommendations by interested parties and IoT and OT considerations will be incorporated into the enhancement process. The agency has not provided a timeframe.
|
| Department of Homeland Security | The Secretary of Homeland Security should direct the Administrator of the Transportation Security Administration and the Commandant of the U.S. Coast Guard to jointly work with the Department of Transportation's Office of Intelligence, Security and Emergency Response, as co-SRMAs for the transportation systems sector, to use the National Plan to develop a sector-specific plan that includes metrics for measuring the effectiveness of their efforts to enhance the cybersecurity of their sector's IoT and OT environments. (Recommendation 5) |
In May 2023, DHS stated that the Transportation Security Administration (TSA), in coordination with the Coast Guard and other DHS offices and divisions and the Department of Transportation, are in the process of updating the 2015 Transportation Systems Sector Specific plan. DHS stated that the publication of the revised sector specific plan is contingent on the release of the revised Presidential Policy Directive 21 (PPD-21) and the National Plan. The President's National Security Memorandum on Critical Infrastructure Security and Resilience (the update to PPD-21) was released in April 2024 and the updated National Plan is due by April 2025. DHS stated that the co-SRMAs anticipate releasing the final updated sector specific plan within six to eight months of the completion of the National Plan.
|
| Department of Homeland Security | The Secretary of Homeland Security should direct the Administrator of the Transportation Security Administration and the Commandant of the U.S Coast Guard to jointly work with the Department of Transportation's Office of Intelligence, Security and Emergency Response, as co-SRMAs for the transportation systems sector, to include IoT and OT devices as part of the risk assessments of their sector's cyber environment. (Recommendation 6) |
In May 2023, DHS stated that the Transportation Security Administration (TSA) hired a cyber risk analyst to incorporate cybersecurity issues in an update to the Transportation Systems Sector Risk Assessment (TSSRA). DHS noted that TSA is working to develop an aviation sector cybersecurity risk methodology that includes consideration of IoT and OT devices found in the airport environment. In addition, DHS stated that the Department of Transportation is consulting with co-SRMA partners on National Security Council-led cybersecurity initiatives and expects to include IoT and OT related risk scenarios in the updated TSSRA by June 28, 2024. We requested a copy of the TSSRA.
|
| Department of Transportation | The Secretary of Transportation should direct the Director, Office of Intelligence, Security and Emergency Response to jointly work with the Administrator of DHS's Transportation Security Administration and the Commandant of the U.S. Coast Guard, as co-SRMAs for the transportation systems sector, to use the National Plan to develop a sector-specific plan that includes metrics for measuring the effectiveness of their efforts to enhance the cybersecurity of their sector's IoT and OT environments. (Recommendation 7) |
In April 2023, Transportation stated that, in coordination with co-SRMA partners at the Department of Homeland Security (DHS), it is developing an update to the 2015 transportation systems sector-specific plan (SSP). It noted that it plans to include metrics for measuring the effectiveness of efforts to enhance the cybersecurity of the sector's IoT and OT environments. In addition, the department stated that the update is dependent on DHS finalizing the National Plan to ensure that the SSP aligns with any substantive changes in the new National Plan. According to the President's National Security Memorandum on Critical Infrastructure Security and Resilience in April 2024, the updated National Plan is due by April 2025.
|
| Department of Transportation | The Secretary of Transportation should direct the Director, Office of Intelligence, Security and Emergency Response to jointly work with the Administrator of DHS's Transportation Security Administration and the Commandant of the U.S. Coast Guard, as co-SRMAs for the transportation systems sector, to include IoT and OT devices as part of the risk assessments of their sector's cyber environment. (Recommendation 8) |
In April 2023, Transportation stated that it will coordinate with co-SRMA partners at the Department of Homeland Security (DHS) to support, as needed, their ongoing efforts to develop Transportation Systems Sector Risk Assessments (TSSRA) and planned to address this recommendation by June 30, 2024. We requested the updated TSSRA.
|
| Office of Management and Budget | The Director of OMB should, as required by the Internet of Things Cybersecurity Improvement Act of 2020, expeditiously establish a standardized process for the Chief Information Officer of each covered agency to follow in determining whether the IoT cybersecurity waiver may be granted. (Recommendation 9) |
On December 2, 2022, OMB issued annual guidance to agencies on the Federal Information Security Management Act and other information security topics, including a section implementing the Internet of Things (IoT) Cybersecurity Improvement Act of 2020. Specifically, OMB's guidance states that CIOs may issue a waiver allowing for the use of certain IoT devices if at least one of the following conditions is met: (1) the waiver is necessary in the interest of national security; (2) procuring, obtaining, or using the IoT device is necessary for research purposes; or (3) the device is secured using alternative and effective methods appropriate to its function. By issuing guidance, OMB provided clarity to agencies on their use of IoT devices in accordance with established statutory waiver criteria or National Institute for Standards and Technology-developed standards and guidelines for IoT device security.
|
