DHS Privacy: Selected Component Agencies Generally Provided Oversight of Contractors, but Further Actions Are Needed to Address Gaps
Fast Facts
The Department of Homeland Security and its contractors collect and maintain large amounts of personally identifiable information (PII)—such as a person's date of birth and social security number.
DHS has developed policies to ensure that its contractors protect PII. These policies include providing privacy training, and overseeing IT systems operated by contractors.
However, DHS didn't fully comply with all of its own policies. For example, DHS headquarters didn't provide all necessary privacy training to contractors.
We made a number of recommendations to DHS to improve its oversight of contractors who handle PII.
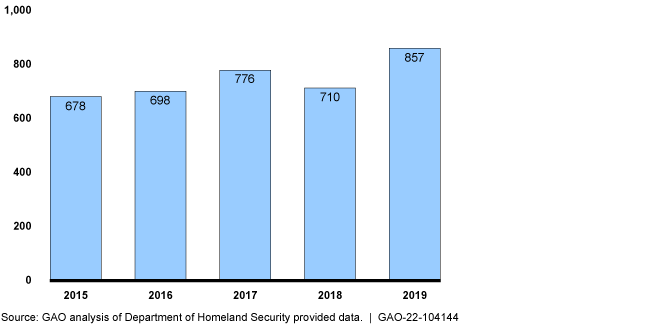
Privacy Incidents Reported to Congress by DHS, 2015-2019
Highlights
What GAO Found
The Department of Homeland Security (DHS) developed policies and procedures to mitigate the risks to personally identifiable information (PII) on contractor-operated IT systems. These policies address federal privacy requirements, standards, and guidelines in the following key areas:
- Establishing and maintaining a comprehensive privacy program.
- Providing agency-wide privacy training for all employees and contractors.
- Overseeing information systems operated by contractors.
- Ensuring implementation of privacy controls for contractor systems.
- Ensuring incident response procedures for contractor systems.
As shown below, selected DHS components addressed most of the key privacy control activities for overseeing contractor-operated systems.
Assessment of Selected DHS Components' Oversight of the Implementation of Privacy Controls in Selected Contractor-Operated Systems
|
Associated activities |
CBP |
DHS HQ |
FEMA |
ICE |
TSA |
USCG |
|
Establish roles and responsibilities |
Met |
Met |
Met |
Met |
Met |
Met |
|
Define privacy requirements in contracts |
Met |
Met |
Met |
Met |
Met |
Met |
|
Identify and address gaps in privacy compliance |
Met |
Met |
Met |
Met |
Met |
Not met |
|
Develop and implement a comprehensive training policy |
Met |
Met |
Met |
Met |
Met |
Met |
|
Administer annual privacy training and targeted role-based privacy training |
Met |
Partially met |
Met |
Met |
Met |
Partially met |
|
Establish and maintain an inventory of all programs and systems with PII |
Met |
Met |
Met |
Met |
Met |
Met |
|
Provide information to contractors describing PII in their possession |
Met |
Met |
Met |
Met |
Met |
Met |
|
Evaluate any proposed new instances of sharing PII with third parties |
Met |
Met |
Met |
Met |
Not met |
Not met |
CBP = U.S. Customs and Border Protection, DHS HQ = Department of Homeland Security headquarters, FEMA = Federal Emergency Management Agency, ICE = Immigration and Customs Enforcement, TSA = Transportation Security Administration, USCG = United States Coast Guard
Met = met associated activities; partially met = partially met associated activities; not met = did not meet associated activities
Source: GAO analysis of agency-provided data.| GAO-22-104144
Although the DHS components complied with most of the requirements, gaps existed. For example, USCG did not demonstrate that it identified and addressed gaps in privacy compliance, DHS HQ did not administer role-based privacy training, and TSA did not demonstrate its evaluation of proposed new instances of PII sharing in contractor-operated systems.
Regarding privacy incidents, DHS developed Privacy Incident Handling Guidance, which outlines the department's process for how incidents are to be identified and remediated. Of the four reviewed components that had a breach of data, three fully identified, remediated, and shared lessons learned for the incidents. However, one component did not document all necessary remediation activities. Fully documenting remediation activities helps ensure that all appropriate steps have been taken to lessen potential harm that the loss, compromise, or misuse of PII could have on affected individuals.
Why GAO Did This Study
It is essential that DHS, its component agencies, and its contractors protect the PII that they collect and maintain. Implementing and enforcing appropriate policies and controls can help prevent improper PII access and use.
GAO was asked to review DHS's policies and procedures for protecting the PII collected by or shared with its contractors. This report discusses the extent to which (1) DHS has developed policies and procedures to mitigate the risks to PII; (2) selected DHS components have provided oversight of privacy controls within contractor-operated systems, and (3) DHS components have ensured that privacy incidents in contractor-operated systems are properly identified and remediated.
GAO analyzed DHS policies and procedures, selected and reviewed six major DHS components, evaluated contractor-operated system documentation related to the oversight of privacy controls, and compared contractor-related privacy incident handling and response activities to DHS requirements. GAO also interviewed relevant officials at DHS and its major components.
Recommendations
GAO is making seven recommendations to DHS components to improve their oversight of contractors' privacy controls and remediation of incidents. DHS concurred with the recommendations and outlined steps planned or taken to address them.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of Homeland Security | The Secretary of the Department of Homeland Security should direct its Privacy Office to provide targeted role-based privacy training to contractors who are responsible for protecting PII. (Recommendation 1) |
As of April 2024, DHS has not provided information pertaining to planned actions for this recommendation. Once the agency states that it has taken action, we plan to verify whether implementation has occurred.
|
| United States Coast Guard | The Commandant of the U.S. Coast Guard should direct the USCG Privacy Office to establish a time frame to complete the development of a process that can be used to identify and assess the gaps in contractor compliance with privacy requirements. (Recommendation 2) |
As of April 2024, the Coast Guard Privacy Office in coordination with the Coast Guard HIPAA Privacy Officer, are drafting an Overarching Medical Program Privacy Impact Assessment (PIA) to describe the use of all laboratory services, medical-related programs, and systems not currently included in the Service's Electronic Health Records Acquisition (eHRA) PIA. In order to close this recommendation, USCG will need to provide information on how the draft Overarching Medical Program PIA will be used to identify and assess the gaps in contractor compliance with privacy requirements.
|
| United States Coast Guard | The Commandant of the U.S. Coast Guard should direct the USCG Privacy Office to ensure, in conjunction with the acquisition office, that contractors certify their acceptance of their privacy requirement responsibilities. (Recommendation 3) |
As of May 2023, the Coast Guard Privacy Office continues to work on the processes for documenting contractor training pertaining to privacy awareness and other privacy-related training required in contractual clauses. In order to close this recommendation, USCG will need to provide documentation that demonstrates contractors certifying their acceptance of their privacy requirement responsibilities.
|
| United States Coast Guard | The Commandant of the U.S. Coast Guard should direct the USCG Privacy Office to ensure the evaluation of proposed new instances of sharing personally identifiable information with third parties are fully documented. (Recommendation 4) |
As of April 2024, the Coast Guard stated that it did not have documentation of new information sharing requests because the specific contractual relationship for laboratory services assessed by GAO did not include new instances of information sharing. The agency added that the Coast Guard Privacy Office reviews all new and updated contracts, including those requiring information sharing outside of the contract scope. In addition, they stated that information sharing requests are documented in the updated contract and reviewed through the DHS-mandated Appendix G process. However, the documentation provided by Coast Guard indicates that it is used during the procurement process and not used for the evaluation of proposed new instances of information sharing. In order to close this recommendation, USCG will need to provide documentation that specifies the process in place to evaluate proposed new instances of sharing PII.
|
| United States Customs and Border Protection | The Commissioner of U.S. Customs and Border Protection should direct the CBP Privacy Office to ensure that risk assessments are fully documented in the incident database. (Recommendation 5) |
In December 2021, we reported that DHS developed the Privacy Incident Handling Guidance (PIHG), which outlines the department's process for how privacy incidents are to be identified and remediated, and for how lessons learned are to be developed and shared with other components. According to the guidance, a series of key actions and activities must be performed to appropriately identify, remediate, and identify lessons learned for privacy incidents, including those that occur within contractor-operated systems. While CBP provided documentation of a completed DHS Risk Assessment Checklist, the findings were not up to date in the incident database as required. The CBP Privacy Branch Chief stated that elements of the risk assessment were interspersed throughout the database; however, we determined that some of the elements in the database, specifically the nature and sensitivity of PII, were outdated and did not reflect the most recent findings identified by CBP in its risk assessment. As a result, we recommended that the CBP Privacy Office ensure that risk assessments are fully documented in the incident database. In response to our recommendation, DHS updated the PIHG to direct DHS Component Privacy Offices to upload all relevant incident information, including, among other things, fully documented risk assessments, for all Component Privacy Officer and Privacy Point of Contact (PPOC)-led incidents to the enterprise incident database. The PIHG also states that the DHS Privacy Office will not close an incident until all requisite information is received from the component. By directing CBP to keep up to date risk assessment findings documented in the incident database, DHS and its components are better equipped to ensure that assessments are accurate and that appropriate mitigation measures have been taken.
|
| United States Customs and Border Protection | The Commissioner of U.S. Customs and Border Protection should direct the CBP Privacy Office to ensure that recommendations to notify affected individuals of privacy incidents are fully documented in the incident database. (Recommendation 6) |
In December 2021, we reported that to ensure incident response procedures are in place for information systems, including those operated by contractors, DHS developed the Privacy Incident Handling Guidance (PIHG), which informs its components, employees, senior officials, and contractors of their obligation to protect PII. Specifically, the guidance outlines the department's process for how privacy incidents are to be identified and remediated, and for how lessons learned are to be developed and shared with other components. According to the guidance, a series of key actions and activities must be performed to appropriately identify, remediate, and identify lessons learned for privacy incidents, including those that occur within contractor-operated systems. CBP did not document recommendations for notification of affected individuals in the incident database. Specifically, CBP Privacy officials determined they did not need to notify affected individuals because the risk of harm was low. CBP Privacy officials stated that notification to affected individuals can be annotated in multiple places within the database; however, they did not provide evidence from the database to document their efforts. As a result, we recommended that the CBP Privacy Office ensure that recommendations to notify affected individuals of privacy incidents are fully documented in the incident database. In response to our recommendation, DHS updated their PIHG to direct DHS Component Privacy Offices to upload all relevant incident information, including, among other things, recommendations to notify affected individuals, for all Component Privacy Officer and Privacy Point of Contact (PPOC)-led incidents to the enterprise incident database. The PIHG also states that the DHS Privacy Office will not close an incident until all requisite information is received from the Component. By directing CBP to fully document notification recommendations for affected individuals, DHS and its components are more able to ensure that they are taking all the appropriate steps to lessen potential harm that the loss, compromise, or misuse of the PII could have on affected individuals.
|
| Transportation Security Administration | The Administrator of the Transportation Security Administration should direct the TSA Privacy Office to ensure the evaluation of proposed new instances of sharing personally identifiable information with third parties are fully documented. (Recommendation 7) |
In response to our recommendation, in June 2022, TSA reported that its Privacy Office added language to its Contract Management Plan template to help ensure the evaluation of proposed new instances of sharing PII with third parties. Specifically, the template states that when a contractor handles PII, they are to coordinate with the TSA Privacy Office or Chief Counsel who will determine whether the Privacy Act applies and identify permissible disclosure of PII outside of DHS. The results of this determination will apply throughout the contract performance. As a result of these actions, TSA is better positioned to reduce the risk that contractors will use shared PII without proper authorization.
|
