SolarWinds Cyberattack Demands Significant Federal and Private-Sector Response (infographic)
The cybersecurity breach of SolarWinds’ software is one of the most widespread and sophisticated hacking campaigns ever conducted against the federal government and private sector. In today’s WatchBlog post, we look at this breach and the ongoing federal government and private-sector response. This information is based on publicly disclosed information from federal and private industry sources. We here at GAO are currently conducting a comprehensive review of the breach with plans to issue a public report later this year.
The breach
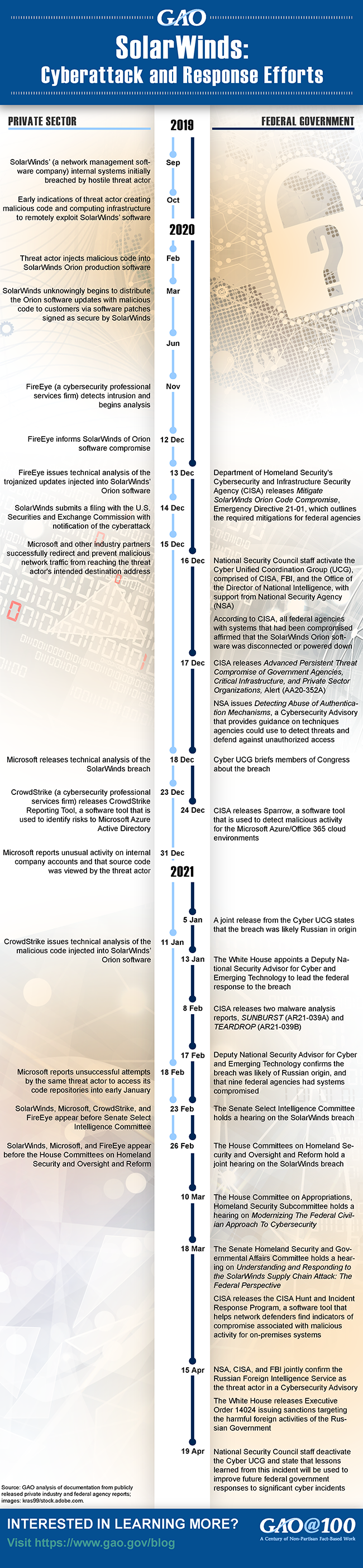
Beginning in September 2019, a campaign of cyberattacks, now identified to be perpetrated by the Russian Foreign Intelligence Service (hereafter referred to as the threat actor), breached the computing networks at SolarWinds—a Texas-based network management software company. The threat actor first conducted a “dry run,” injecting test code into SolarWinds’ network management and monitoring suite of products called Orion. Then, beginning in February 2020, the threat actor injected trojanized (hidden) code into a file that was later included in SolarWinds’ Orion software updates. SolarWinds released the software updates to its customers not realizing that the updates were compromised. The trojanized code had provided the threat actor with a “backdoor”—a program that can give an intruder remote access to an infected computer. According to cybersecurity researchers, the threat actor was then able to remotely exploit the networks and systems of SolarWinds’ customers who had downloaded the compromised software updates using a sophisticated computing infrastructure.
Since SolarWinds is widely used in the federal government to monitor network activity on federal systems, this incident allowed the threat actor to breach infected agency information systems. SolarWinds estimates that nearly 18,000 of its customers received a compromised software update. Of those, the threat actor targeted a smaller subset of high-value customers, including the federal government, to exploit for the primary purpose of espionage.
Discovery and response: What now?
FireEye—a cybersecurity professional services firm—stated that in November 2020 it had detected an intrusion to its systems and later informed SolarWinds of the compromise of the Orion platform. In addition, in coordination with FireEye, Microsoft reported the threat actor was able to compromise some of Microsoft’s cloud platforms. The compromise allowed the threat actor to gain unauthorized network access. Microsoft informed several federal agencies that their unclassified systems had been breached and took steps with other industry partners to redirect the malicious network traffic away from the domain used by the threat actor to render the malicious code ineffective and prevent further compromise.
In response to this breach, on December 13, 2020, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) released an emergency directive outlining required mitigations for federal agencies to prevent further exploitation of federal information systems. On December 16, the White House’s National Security Council activated the Cyber Unified Coordination Group, who is responsible for coordinating the government-wide response to the incident. This group includes officials from the Office of the Director of National Intelligence, FBI, and CISA, with support from the National Security Agency.
GAO and Congressional monitoring will continue
Congress held multiple hearings to gather and report information on the timeline of events related to the SolarWinds hack, and larger issues such as IT supply chain security (meaning the security of information and communications technology products and services), threat actor capability and motivation, and future federal actions and improvements.
Although our examination of SolarWinds is ongoing, we have previously reported on IT supply chain risks and major cybersecurity challenges. We continue to emphasize that the federal government needs to move with greater urgency to improve the nation's cybersecurity as the country faces grave and rapidly evolving threats. Ensuring the cybersecurity of the nation has been on our High Risk List since 1997.
A detailed timeline of federal government and private sector activities to remediate the breach is illustrated in the graphic below.
- Comments on GAO’s WatchBlog? Contact blog@gao.gov.
GAO Contacts
Related Products

GAO's mission is to provide Congress with fact-based, nonpartisan information that can help improve federal government performance and ensure accountability for the benefit of the American people. GAO launched its WatchBlog in January, 2014, as part of its continuing effort to reach its audiences—Congress and the American people—where they are currently looking for information.
The blog format allows GAO to provide a little more context about its work than it can offer on its other social media platforms. Posts will tie GAO work to current events and the news; show how GAO’s work is affecting agencies or legislation; highlight reports, testimonies, and issue areas where GAO does work; and provide information about GAO itself, among other things.
Please send any feedback on GAO's WatchBlog to blog@gao.gov.




