Recent Cyberattacks Further Highlight Need For Action
Recent high-profile and widespread cyberattacks on federal agencies and national infrastructure have further highlighted the need for the government to address this attack and prevent future ones. However, these threats and the challenges in addressing them are long-standing and have earned cybersecurity a spot on GAO’s High Risk List since the 1990s.
In today’s WatchBlog, we look at why federal agencies and our nation’s critical infrastructure—such as energy, communications, and financial services—are prime targets for cyberattacks, and the challenges in protecting them.
Recent cyberattack
In December, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) reported that an advanced, persistent threat had inserted a “backdoor”—a malicious program that can potentially give an intruder remote access to an infected computer—into a genuine version of a network management software product. The malicious actor used this backdoor, among other techniques, to initiate a cyberattack campaign against U.S. government agencies, critical infrastructure entities, and private-sector organizations that use the compromised network management software product. According to CISA, this threat poses a grave risk to the federal agencies and our nation’s critical infrastructure, among others.
We have begun reviewing the federal response to the recent cyberattack. We will be monitoring these efforts and reporting back.
Ensuring the cybersecurity of the nation
This most recent attack further highlights the urgent need to address the long-standing cybersecurity challenges facing the nation. We designated information security as a government-wide high risk area in 1997. More recently, we identified 4 major cybersecurity challenges and 10 critical actions that the federal government and other entities need to take to address those challenges. The figure below outlines these actions.
Figure: 10 Critical Actions Needed to Address 4 Major Cybersecurity Challenges
Image
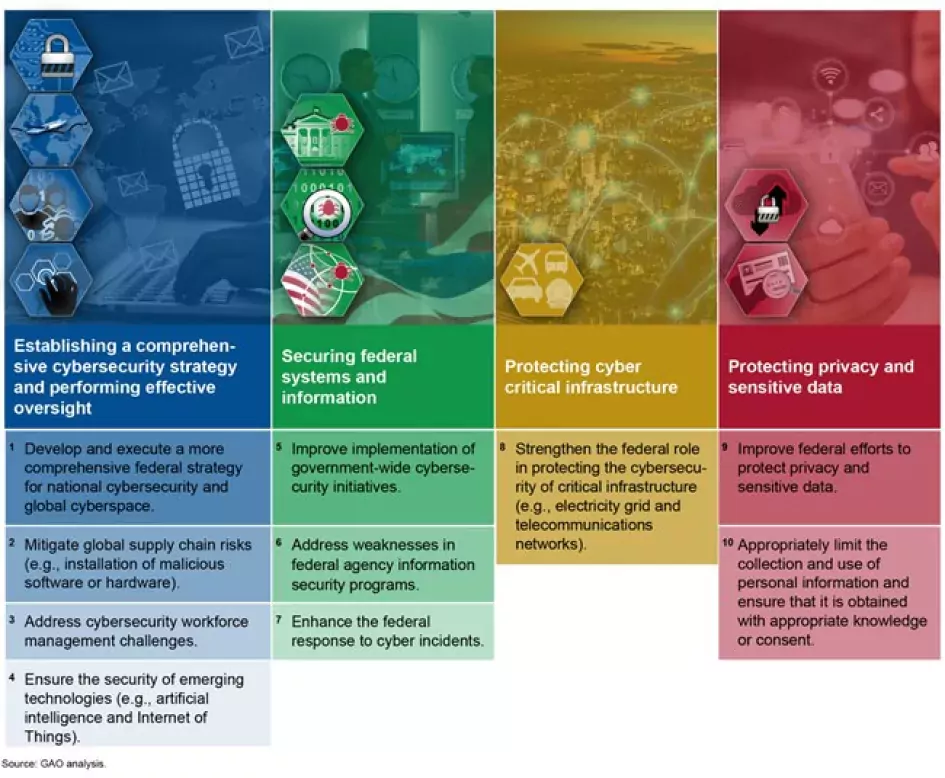
The complexity and severity of the recent attack means that the federal government needs to implement multiple actions simultaneously. For example:
- Develop and execute a more comprehensive federal strategy for national cybersecurity and global cyberspace. In September, we highlighted the urgent need to clearly define a central leadership role for coordinating the federal strategy on national cybersecurity. Earlier this month, Congress established the Office of the National Cyber Director within the Executive Office of the President. The National Cyber Director will be responsible for integrating cybersecurity policy and operations across the executive branch. But the position must be filled in order to coordinate implementation of a national cyber strategy, including activities needed to effectively respond to significant cybersecurity incidents.
Listen to our podcast below with GAO’s Nick Marinos about cyber strategy and leadership to learn more.
- Mitigate global supply chain risks. We also reported in December that none of the 23 agencies in our review had fully implemented the 7 selected practices for managing information and communications technology (ICT) supply chain. For example, only 3 of the agencies had developed organizational procedures to detect counterfeit and compromised ICT products prior to deployment. As a result, we made 145 recommendations, which still need to be implemented to address those weaknesses.
To learn more, listen to our December podcast with GAO’s Carol Harris about supply chain cybersecurity.
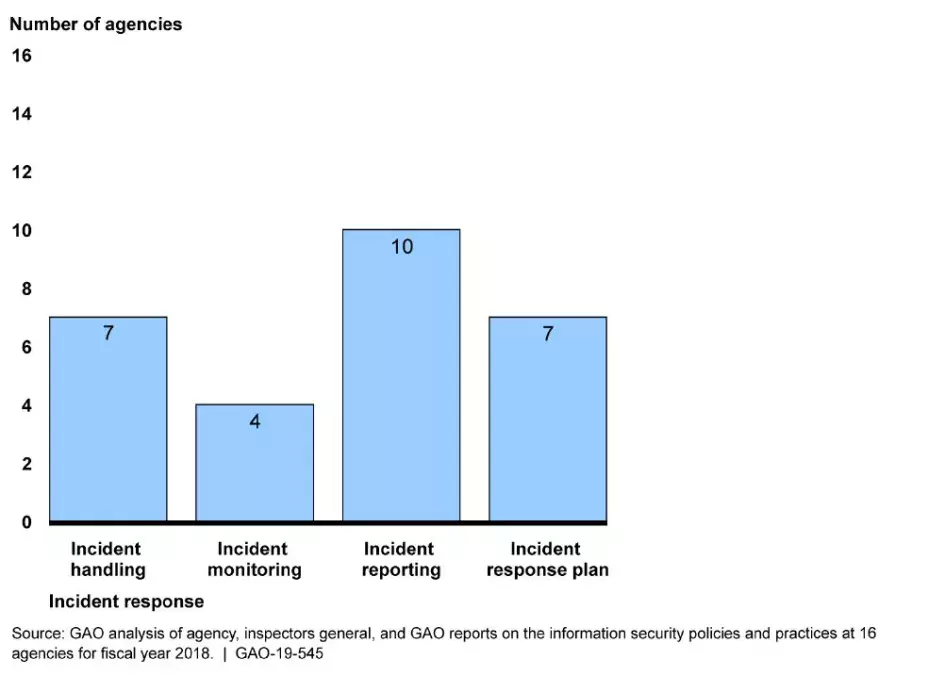
- Enhance the federal response to cyber incidents. In July 2019, we reported that most of 16 selected federal agencies were deficient in at least 1 of the activities associated with incident response processes. For example, 7 of the 16 agencies did not adequately implement capabilities to analyze and respond to security incidents. In addition, 10 agencies did not consistently categorize incidents or ensure timely reporting of incidents. The figure below illustrates these deficiencies. We and the Inspectors General have made thousands of recommendations aimed at improving information security programs and practices—including those relating to incident response processes over the years. However, many of these recommendations remain unimplemented.
Figure: The Number of 16 Selected Agencies with Deficiencies in Incident Response
Image