The Quest to Combat Insider Threats at Our Nation’s Airports
For many, the presence of Transportation Security Administration (TSA) personnel screening passengers can bring a sense of security that nefarious actors won’t get past the airport’s checkpoints. But have you ever wondered how you are protected if the screeners or other airport workers are the nefarious actors? Many of these workers have access within restricted areas of the airport, would know details of the airport’s security procedures, and could exploit vulnerabilities to engage in illicit activities like smuggling illegal goods.
In today’s WatchBlog, we explore our recent work on the TSA Insider Threat Program that aims to deter, detect, and mitigate insider threats at the nation’s approximately 430 TSA-regulated airports.
Image

How does TSA secure so many airports from insider threats?
To ensure the security of airports that it regulates, TSA collaborates with airport management, airlines, law enforcement, and other entities to implement security programs. Although these programs vary across airports, all are designed to mitigate threats to aviation security, including preventing TSA and other airport workers from causing harm—intentional or otherwise. Such harm could take the form of a screener who willfully allows a bag of drugs through the X-ray machine; an aircraft mechanic who sabotages passenger safety equipment; or an airport worker who carries a bag of firearms through a restricted-access door to a passenger. TSA is on the lookout for all of them.
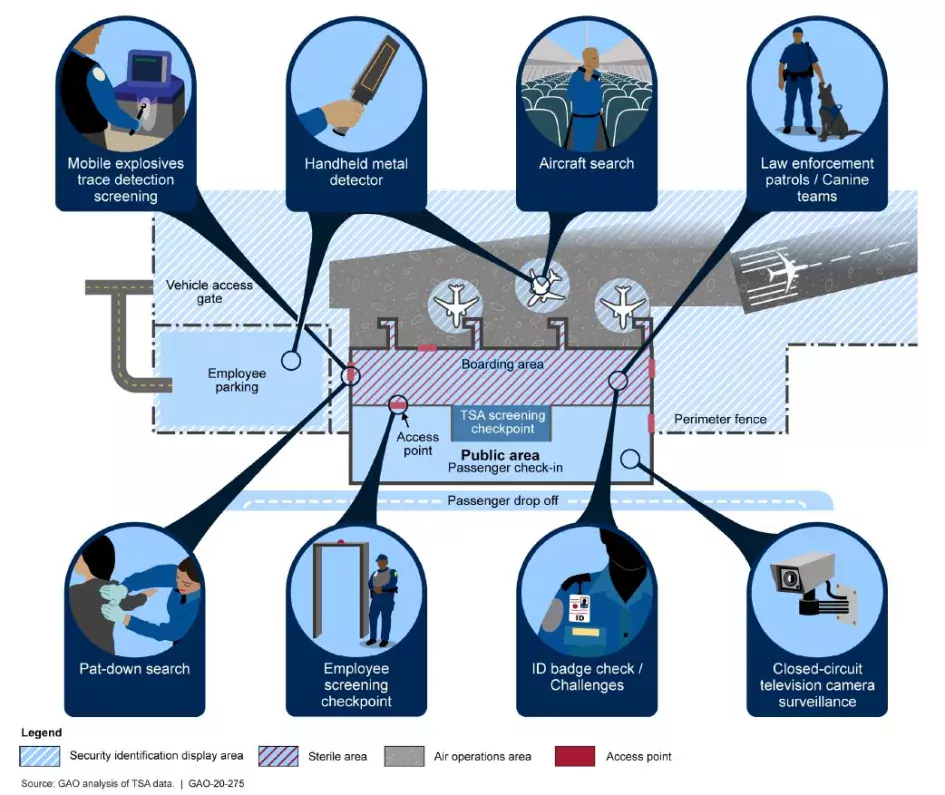
There are approximately 1.8 million airport workers across the U.S. who are monitored by security measures approved by or carried out by TSA, such as:
- vetting prospective employees,
- restricting access to sensitive areas by using badge readers and biometric sensors,
- randomly searching workers, and other measures highlighted in the figure below.
Figure: Examples of Security Procedures and Technologies Used by TSA or Other Aviation Stakeholders to Help Mitigate Insider Threats at TSA-Regulated Airports
Image
Is there anything new with TSA’s insider threat programs?
In 2018, TSA updated their efforts to mitigate insider threats, including analyzing social media accounts to help “vet” select prospective employees applying for a position with access within restricted areas of an airport.
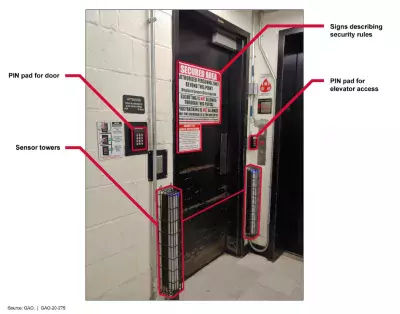
In fact, our analysis showed that the management at many airports are taking additional measures beyond TSA requirements to improve security. For example, to prevent a second worker from entering a restricted area by “piggybacking” behind another worker who swiped his badge, one airport we visited installed sensor towers (shown below) to detect if more than one person crosses the threshold.
Figure: Access Control Technologies at an Access Point to a Secured Area of an Airport
Image
These efforts to keep our airports secure require coordination across multiple offices and committees within TSA. This makes it challenging for the agency to synchronize and integrate activities across offices. TSA would benefit from a strategic plan or roadmap for the Insider Threat Program. We recommended that TSA develop such a plan, as well as identify ways to measure the program’s progress in detecting and deterring insider threats.
To learn more about our recommendations to improve TSA’s Insider Threat Program, check out our report.
GAO Contacts
Related Products

GAO's mission is to provide Congress with fact-based, nonpartisan information that can help improve federal government performance and ensure accountability for the benefit of the American people. GAO launched its WatchBlog in January, 2014, as part of its continuing effort to reach its audiences—Congress and the American people—where they are currently looking for information.
The blog format allows GAO to provide a little more context about its work than it can offer on its other social media platforms. Posts will tie GAO work to current events and the news; show how GAO’s work is affecting agencies or legislation; highlight reports, testimonies, and issue areas where GAO does work; and provide information about GAO itself, among other things.
Please send any feedback on GAO's WatchBlog to blog@gao.gov.




