Protecting Critical Infrastructure from Cyberattacks
The nation’s critical infrastructures —such as energy, transportation systems, communications, and financial services—are dependent on information technology (IT) systems and electronic data to carry out and report on operations. But these systems are increasingly at risk from things like insider threats from witting or unwitting employees and emerging cyber threats from around the globe.
In today’s WatchBlog, we look at the growing risks that put cybersecurity on GAO’s High Risk List, and ways the federal government could better safeguard critical infrastructure.
We spoke with three of GAO’s experts on cybersecurity of critical infrastructure, Bill Russell, Neelaxi Lakhmani, and Kaelin Kuhn, in our latest Watchdog Report: Deep Dig Episode. Listen, and read on for more.
Guard the grid
The U.S. electric grid is vulnerable to cyberattacks, particularly on the systems that control electric power generation, transmission, and distribution. These systems were once isolated from the internet, but now they’re increasingly connected. In addition, recent federal assessments indicate that cyberattacks could cause widespread power outages in the United States, but the scale of such outages is uncertain.
The Department of Energy (DOE) plays a key role in helping address cybersecurity risks in the electric grid’s infrastructure. However, the DOE has not developed plans and assessments for electric grid cybersecurity that address the key characteristics needed for a national strategy. For example, DOE’s risk assessment had significant methodological limitations; it used a model that covered only a portion of the grid and reflected how that portion existed around 1980. We recommended that DOE develop a plan for electric grid cybersecurity that addresses the key characteristics needed for a national strategy—including a full assessment of cybersecurity risks to the grid.
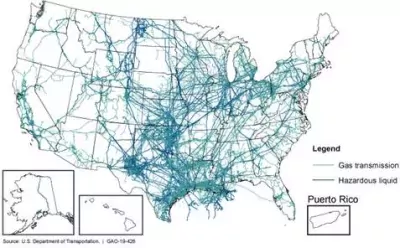
Secure the pipelines
More than 2.7 million miles of pipeline transport the natural gas, oil, and other hazardous liquids the nation needs. Most pipeline systems are monitored using remote sensors, signals, and preprogrammed parameters. These computerized systems are attractive targets for hackers and terrorists. A minor pipeline system disruption could result in commodity price increases; a major disruption could cause widespread energy shortages.
In 2010, the Transportation Security Administration issued a plan to coordinate responses to pipeline security incidents among government agencies and with the private sector. However, TSA has not updated this plan since its issuance, so it doesn’t fully reflect developments in key areas like cybersecurity. We recommended that TSA periodically review and update this plan.
Standardize national security
The National Institute of Standards and Technology created a framework of cybersecurity standards and procedures that federal agencies can use to address cybersecurity threats. We looked at how federal agencies that are responsible for the nation’s critical infrastructure used this framework.
We found that all the federal agencies we looked at were voluntarily using the framework and have seen benefits. For example, one agency said that the framework allowed it to better identify and address cybersecurity risks. However, we found that some agencies are not collecting or reporting on improvements from using the framework. Until they do so, it will be difficult to determine if this framework is effectively protecting critical infrastructure from cyberattacks.
To learn more about these issues, check out our reports on securing the electric grid and pipelines, as well as the cybersecurity framework.
- Comments on GAO’s WatchBlog? Contact blog@gao.gov