Government IT Systems Still at Risk
Lately, it’s a recurring news story—another hack, leak, or breach, and sensitive information is compromised. We’ve long identified information system security as a high-risk area throughout the government. So for October’s Cybersecurity Awareness Month, we’re highlighting federal cybersecurity challenges.
Secure systems to secure the nation
Reported cybersecurity incidents at federal agencies grew more than twelvefold from 2006 to 2014.
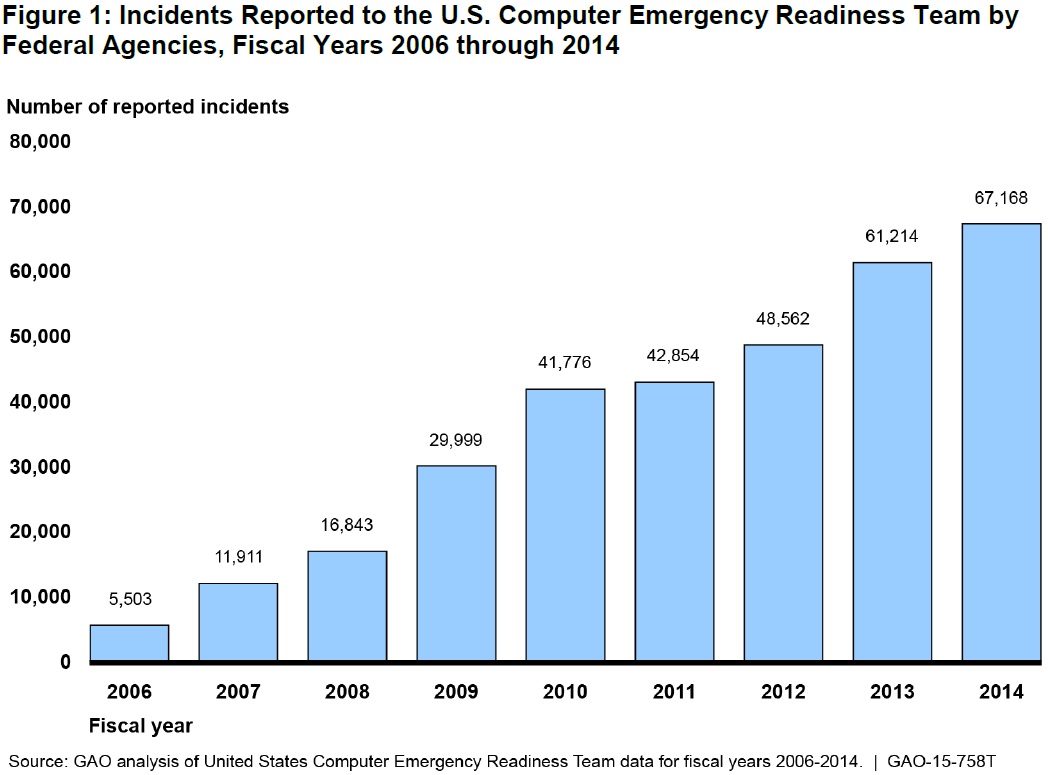 (Excerpted from GAO-15-758T)
(Excerpted from GAO-15-758T)
These incidents can result in the release of sensitive and personal information, theft of intellectual property, destruction or disruption of critical systems, and damage to economic and national security.
Agencies are supposed to protect themselves against threats from hackers, terrorists, insiders, and other nations. To secure federal IT systems, agencies should
- limit access or detect who accesses programs, computers, and facilities
- prevent unauthorized changes to programs and computers
- split responsibilities so no single person controls everything
- plan for problems to keep operations running during emergencies
- manage security so risks are understood and addressed.
But agencies have struggled to implement these security measures. In fact, we found that most of the 24 major federal agencies had persistent weaknesses in 3 or more of these areas. These weaknesses could expose confidential information or even take down entire systems.
It’s getting personal
Despite the vast amount of information they collect, agencies don’t always have policies and procedures to assess risks and protect the personal information of citizens and residents.
For example, in 2014 we reported that the Centers for Medicare & Medicaid Services hadn’t fully assessed privacy risks related to systems supporting Healthcare.gov, the federal health insurance marketplace. Until these and other weaknesses are addressed, Healthcare.gov and its related systems face unnecessary risks.
Critical threats to critical infrastructure
The nation’s critical infrastructure is also vulnerable to cyberattacks. Most of that infrastructure—power plants, phone lines, hospitals—is owned and operated by the private sector, which means that the private sector and the government have to work closely together to protect these critical assets.
However, federal agencies haven’t always been on top of this. For instance, we recently found that the FAA had significant weaknesses in securing air traffic control systems. If these weaknesses were exploited, the impact on air safety could be devastating. Listen to Greg Wilshusen, a director in our Information Technology team, explain:
Fixes, not patches
The proliferation of cyber threats makes cybersecurity a daunting challenge for the federal government. To help meet these challenges, we have made hundreds of recommendations aimed at strengthening agencies’ cybersecurity. It will take coordinated effort across the government, with strong strategic direction from the White House and effective oversight, to make sure that federal agencies are taking all the necessary steps to protect our nation’s systems and information.
- Questions on the content of this post? Contact Greg Wilshusen at wilshuseng@gao.gov.
- Comments on GAO’s WatchBlog? Contact blog@gao.gov.





